Image detection and attachment analysis
Did you know ?
is the victim of a phishing attack containing a malicious attachment.
To bypass the security systems that analyze messages, hackers use images or QRCodes to convey their threats.. QRCodes take you to malicious links, and images can contain instructions (for example: "go to url xxx", or "to open the ZIP file in PJ, please use the password blablabla"...).
In the face of these cyberthreats, Secuserve has the ability to detect these traps and image forms. In fact, our solution can analyze your attachments in depth and transform your images into text to identify the following problems.
How the solution works!
Our systemsidentify he various attachments included in your e-mails.
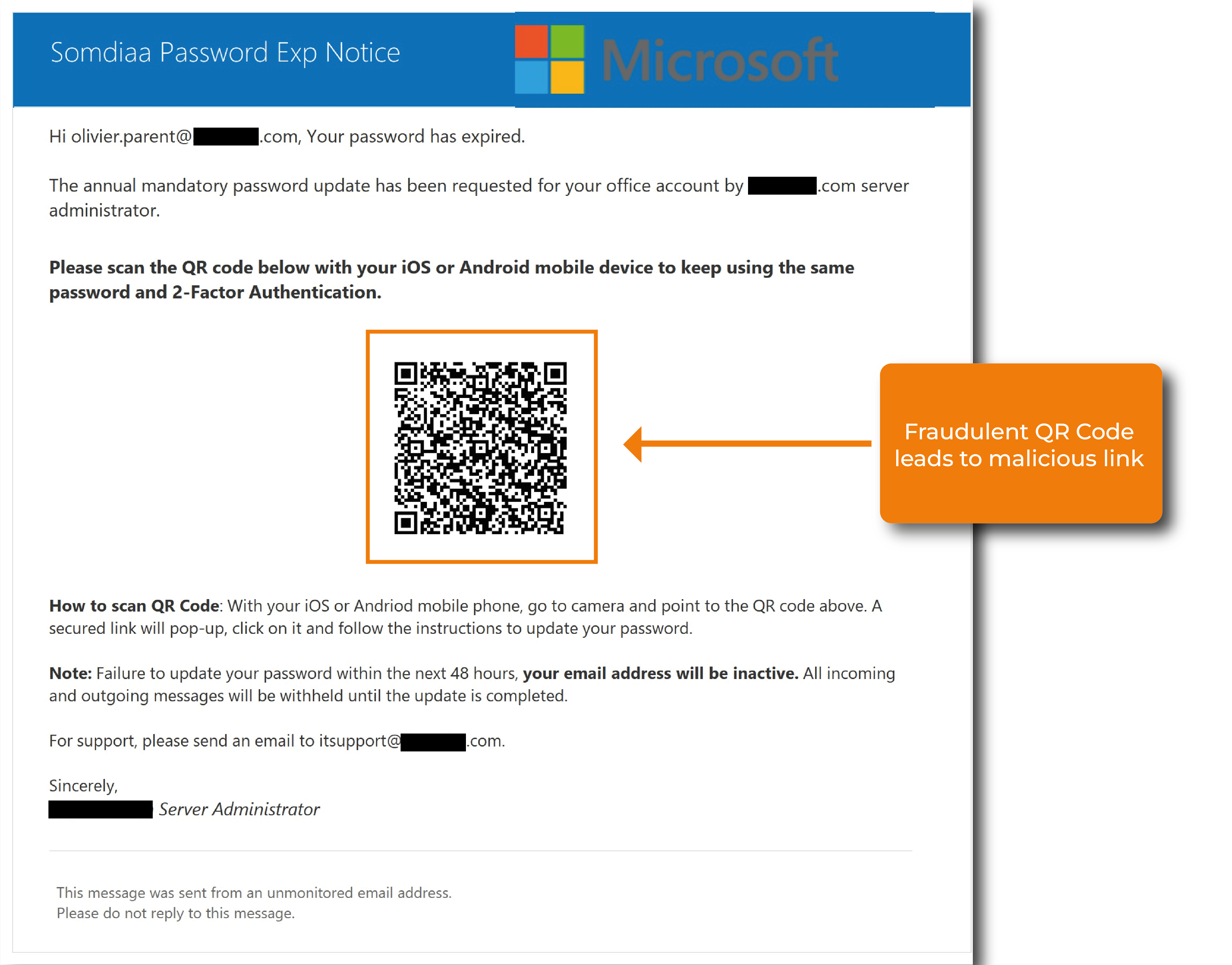
We examine the following cases Fraudulent QR Code (with related information or text)
Detection of image files (SVG, JPEG, PNG, GIF, etc.): Our e-securemail solution analyzes a typical scamming category (e.g. sextortion, lotteries, fictitious gifts, social engineering, fraudulent ads, etc.).
Les File extensionscan be forged or counterfeited. Identifying the file extension is not a reliable way of determining whether a file is safe or not.
That's why we also analyze other common files fichiers :
Microsoft Word : .doc, .docx (DOC, DOCX), Microsoft Excel : .xls, .xlsx (XLS, XLSX), Adobe Acrobat : .pdf (PDF), executable files: .exe, .app (EXE, APP),
archive files : .zip, .rar, .iso (ZIP, RAR, ISO), plain text files: : .txt (TXT).

Setting the scene
Almost any file can be attached to an e-mail. Nevertheless, like any file sent over a network, attachments can sometimes contain dangerous or malicious content that could infect a device with malware. Similarly, they can help cybercriminals to steal your personal or financial information via techniques such as "QR code phishing" or "quishing".
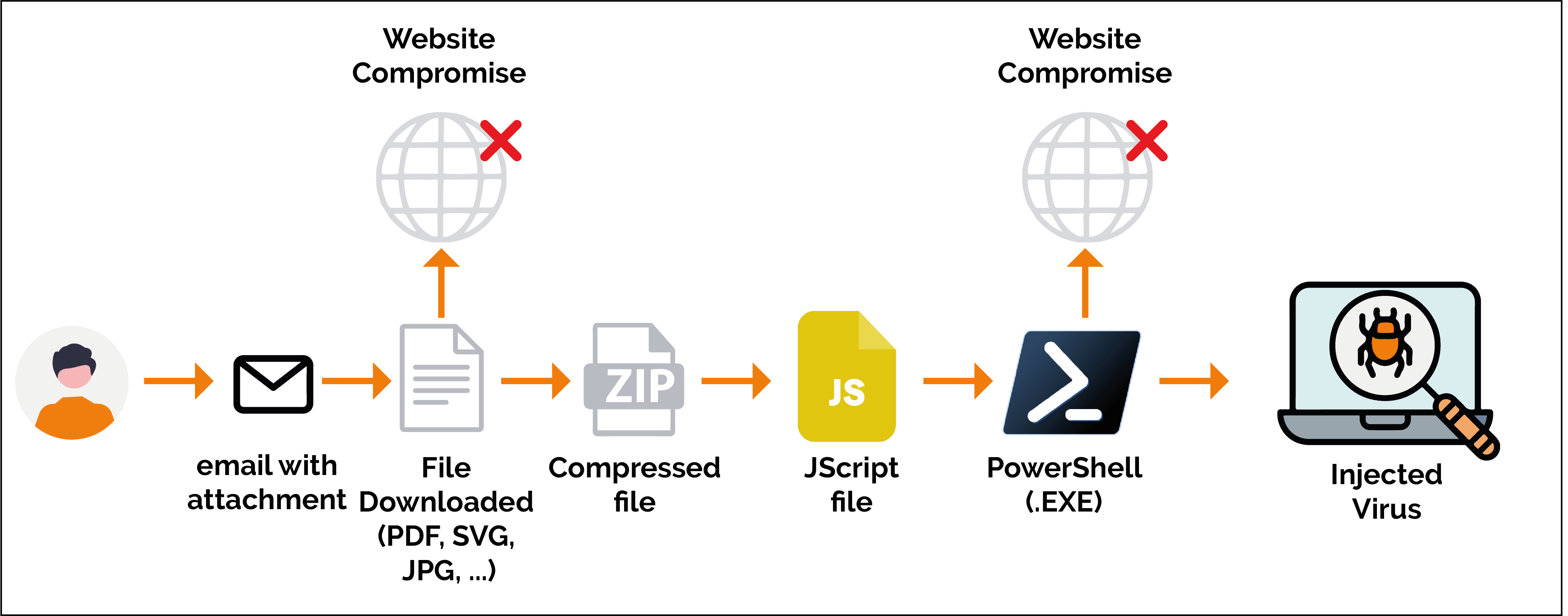
Case 1: Virus injection
Hackers often try to spread malware by attaching it to e-mails. Sometimes, they attach malware in the form of an executable file (EXE) and entice the recipient to download and open the file, enabling the malware to run. Other times, they may hide a malicious script in an innocuous-looking file, such as a Microsoft Word document (DOC, DOCX) or an archive file (ZIP, RAR, etc.). Once the script has been executed, it downloads and installs malware or performs some other malicious action.
Finally, attackers can hide malware or scripts in file types that seem unlikely to contain them, such as images or video files. Any type of file can contain malicious code. Archive files, PDFs, Microsoft Word documents and Microsoft Excel spreadsheets have been used in many malware attacks. However, attackers are not limited to these file types. Everything from images to text files can be dangerous.
Objective : Include a malicious macro in a document and prompt the user to click, enabling the macro to infect the computer.
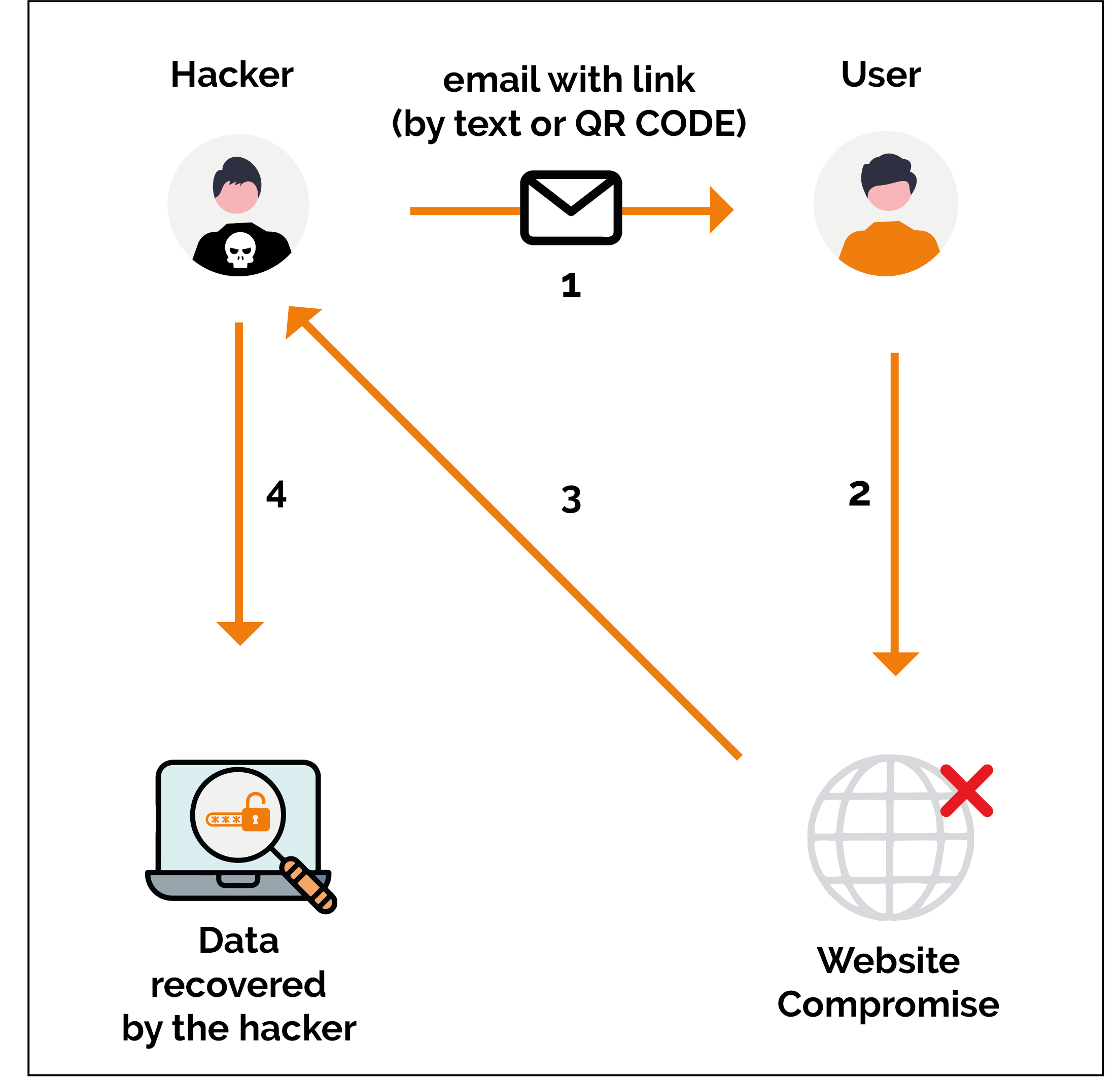
Case 2: Attempted quishing
Cybercriminals create QR codes which they associate with a legitimate call to action, inviting users to scan the code. This could be an offer such as a gift or coupon, or a link to a survey. They affix these QR codes and fraudulent messages to your e-mails.
By scanning the QR code, the victim is taken to a website that appears to match what the call to action promised, but which is in fact administered by the hacker. On this site, the victim is invited to enter personal data such as name, e-mail address, telephone number or postal address.
They are often prompted to enter credit card, bank account or other login details. In some cases, victims are asked to download an application or file containing malware.
Objective : to steal personal, banking and/or financial information.
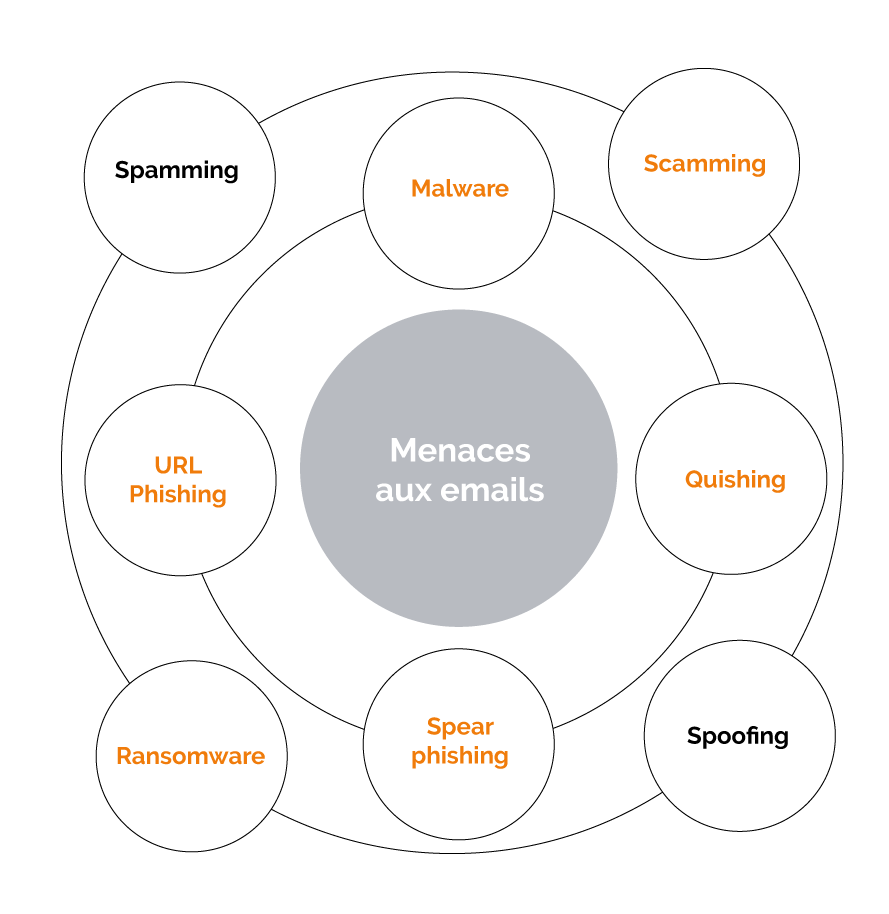
Types of cyberthreats treated